Introduction
Information and operational technology (IT/OT) rely on a complex, globally distributed, and interconnected supply chain ecosystem to provide highly refined, cost-effective, and reusable solutions. This ecosystem is composed of various entities with multiple tiers of outsourcing, diverse distribution routes, assorted technologies, laws, policies, procedures, and practices, all of which interact to design, manufacture, distribute, deploy, use, maintain, and manage IT/OT products and services.
Cybersecurity in the supply chain cannot be viewed as an IT problem only. Cyber supply chain risks touch sourcing, vendor management, supply chain continuity and quality, transportation security, and many other functions across the enterprise and requires a coordinated effort to address.
Organizations are increasingly at risk of supply chain compromise, whether intentional or unintentional. The factors that allow for low-cost, interoperability, rapid innovation, a variety of product features, and other benefits, also increase the risk of a compromise to the cyber supply chain, which may result in risks to the end-user. Managing cyber supply chain risks requires ensuring the integrity, security, quality, and resilience of the supply chain and its products and services.
Cyber supply chain risks may include the insertion of counterfeits, unauthorized production, tampering, theft, insertion of malicious software and hardware, as well as poor manufacturing and development practices in the cyber supply chain.
Related: The Functional Roles of IT in Supply Chain Management

Cyber Supply Chain Security Principles
Develop your defenses based on the principle that your systems will be breached. When one starts from the premise that a breach is inevitable, it changes the decision matrix for the next steps. The question becomes not just how to prevent a breach, but how to mitigate an attacker’s ability to exploit the information they have accessed and how to recover from the breach.
Cybersecurity is never just a technology problem, it’s a people, processes, and knowledge problem. Breaches tend to be less about a technology failure and more about human error. IT security systems won’t secure critical information and intellectual property unless employees throughout the supply chain use secure cybersecurity practices.
Security is Security. There should be no gap between physical and cybersecurity. Sometimes the bad guys exploit lapses in physical security in order to launch a cyber attack. By the same token, an attacker looking for ways into a physical location might exploit cyber vulnerabilities to get access.
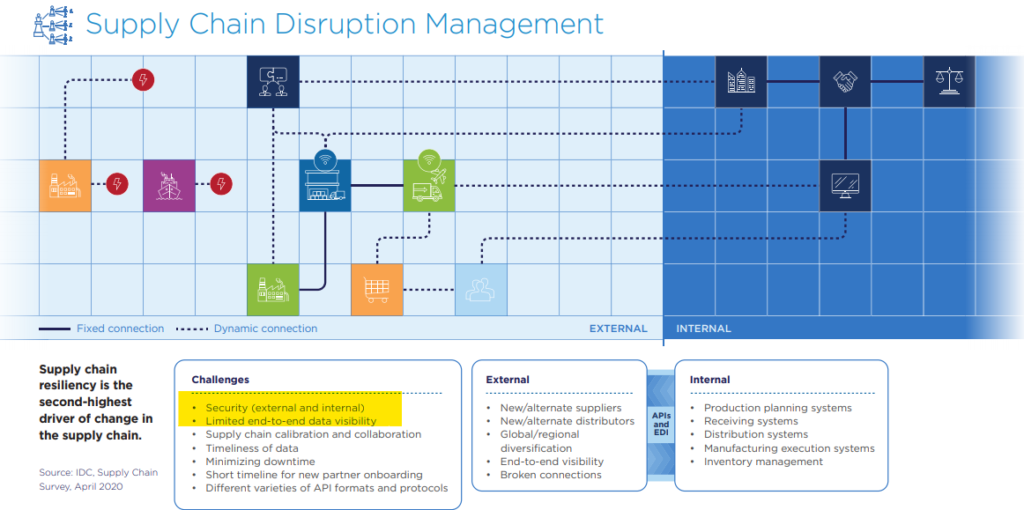
Supply Chain Focus Areas
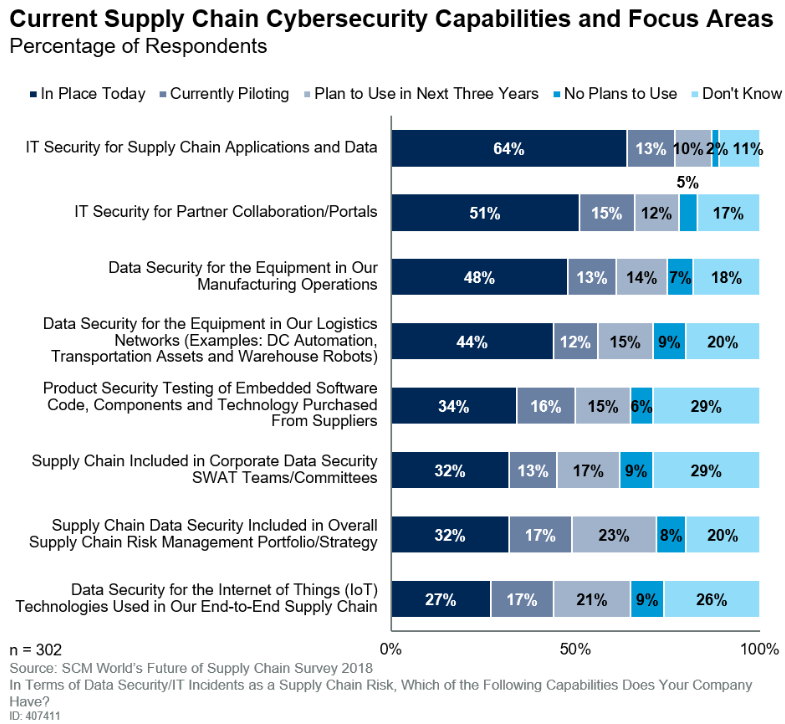
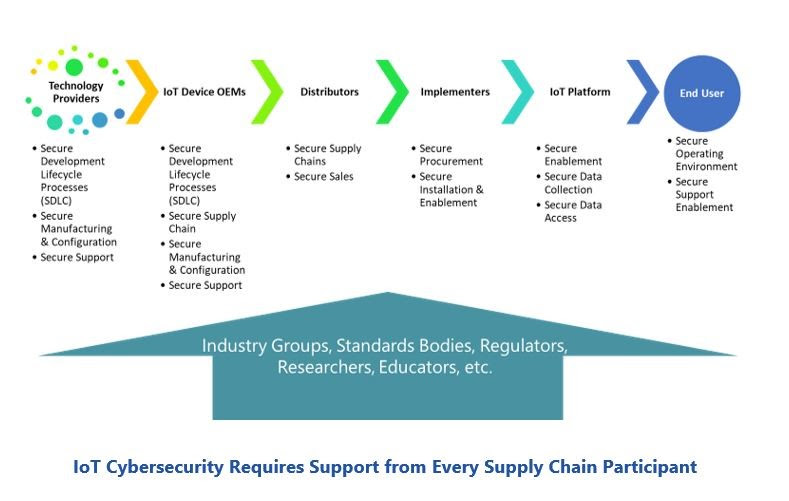
Key Cyber Supply Chain Risks
Cyber supply chain risks cover a lot of territories. Some of the concerns include risks from:
- Third-party service providers or vendors – from janitorial services to software engineering — with physical or virtual access to information systems, software code, or IP.
- Poor information security practices by lower-tier suppliers.
- Compromised software or hardware purchased from suppliers.
- Software security vulnerabilities in supply chain management or supplier systems.
- Counterfeit hardware or hardware with embedded malware.
- Third-party data storage or data aggregators.
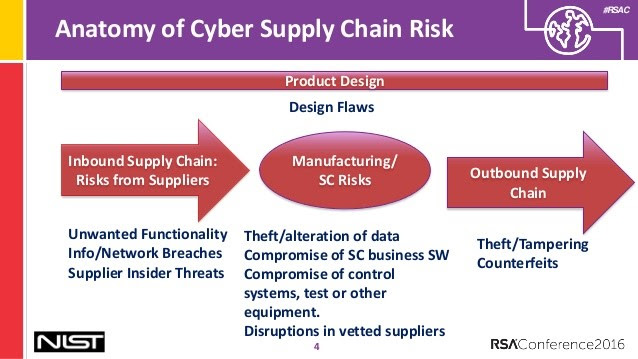
Examples of Cybersecurity Questions
Companies are using the following questions to determine how risky their suppliers’ cybersecurity practices are:
- Is the vendor’s software/hardware design process documented? Repeatable? Measurable?
- Is the mitigation of known vulnerabilities factored into product design (through product architecture, run-time protection techniques, and code review)?
- How does the vendor stay current on emerging vulnerabilities? What are vendor capabilities to address new “zero-day” vulnerabilities?
- What controls are in place to manage and monitor production processes?
Quality assurance
- How is configuration management performed? How is it tested for code quality or vulnerabilities?
- What levels of malware protection and detection are performed?
- What steps are taken to “tamper-proof” products? Are the back doors closed?
- What physical security measures are in place? Documented? Audited?
- What access controls, both cyber and physical are in place? How are they documented and audited?
- How do they protect and store customer data?
- How is the data encrypted?
- How long is the data retained?
- How is the data destroyed when the partnership is dissolved?
- What type of employee background checks are conducted and how frequently?
- What security practice expectations are set for upstream suppliers?
- How is adherence to these standards assessed?
- How secure is the distribution process?
- Have approved and authorized distribution channels been clearly documented?
- What are the component disposal risk and mitigation strategies?
- How does the vendor assure security through the product life cycle?
Examples of Cyber Supply Chain Best Practices
Companies have adopted a variety of practices that help them manage their cyber supply chain risks. These practices include:
- Security requirements are included in every RFP and contract.
- Once a vendor is accepted in the formal supply chain, a security team works with them on-site to address any vulnerabilities and security gaps.
- “One strike and you’re out” policies with respect to vendor products that are either counterfeit or do not match specifications.
- Component purchases are tightly controlled; component purchases from approved vendors are prequalified. Parts purchased from other vendors are unpacked, inspected, and x-rayed before being accepted.
- Secure Software Lifecycle Development Programs and training for all engineers in the life cycle are established.
- Source code is obtained for all purchased software.
- Software and hardware have a security handshake. Secure booting processes look for authentication codes and the system will not boot if codes are not recognized.
- Automation of manufacturing and testing regimes reduces the risk of human intervention.
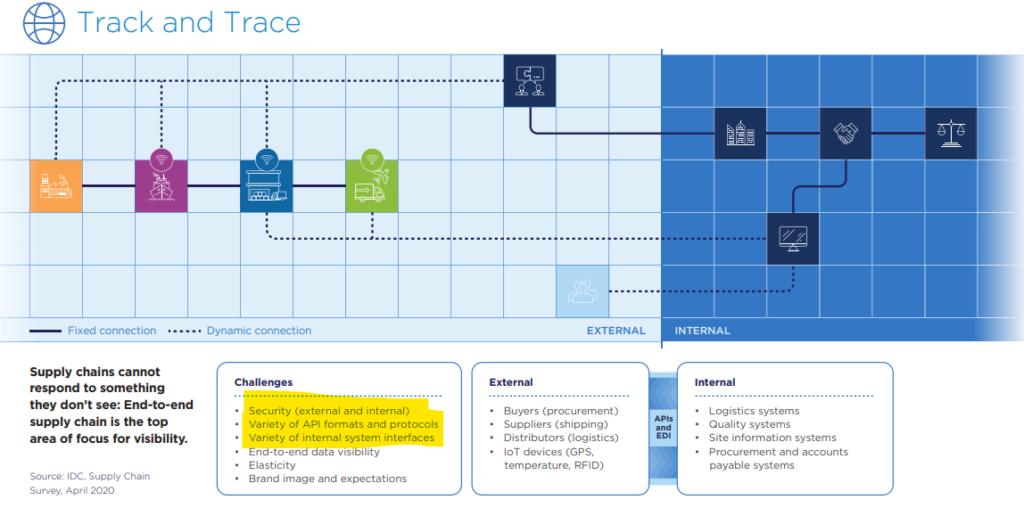
Track and Trace
Track and trace programs establish the provenance of all parts, components, and systems.
- Programs capture “as-built” component identity data for each assembly and automatically link the component identity data to sourcing information.
- Personnel in charge of supply chain cybersecurity partner with every team that touches any part of the product during its development lifecycle and ensures that cybersecurity is part of suppliers’ and developers’ employee experience, processes, and tools.
- Legacy support for end-of-life products and platforms; assure continued supply of authorized IP and parts.
- Tight controls on access by service vendors are imposed. Access to the software is limited to very few vendors. Hardware vendors are limited to mechanical systems with no access to control systems. All vendors are authorized and escorted.

Danish Mairaj is a medical device expert with a strong focus on regulatory and quality compliance. He has been involved in managing clinical trial infrastructure including supplies and logistics. He has over 15 years of experience in the MedTech and Pharmaceutical industry. He is a certified Product Owner, Scrum Master, and Project Management Professional PMP. He studied Biomedical Engineering in Germany and MedTech Regulatory & Quality in Galway, Ireland. He contributes articles to the BRASI newsletter.
- Danish Mairaj#molongui-disabled-link








